How To: Lock Down Your Google Account with Google's New Physical Key
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.Passwords and PINs can easily be hacked, and if your password were ever leaked onto the web, or your bank PIN discovered, there would be no other security barrier to prevent a hacker or thief from accessing your account besides maybe some "strong" authentication challenge questions.That's why some companies have implemented two-step verification (and even the more secure multi-factor authentication) for their websites. Apple currently offers two-step verification for Apple IDs, and Google also offers it for Google Accounts.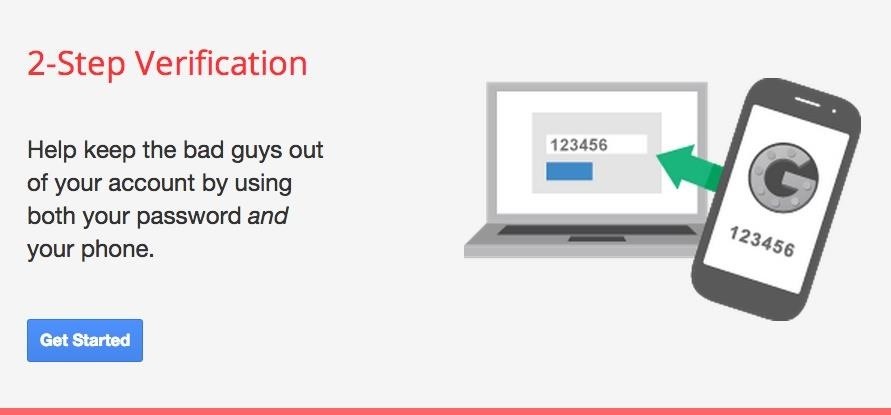
How 2-Step Verification Works for Google AccountsFirst, a user logs into their device using their regular password. Once that password is confirmed, a code will be sent to your mobile device (one previously set up with the two-step verification process). Next, the user enters in the verification code that they received on their device in order to finally log in. Google states: "2-Step Verification adds an extra layer of security to your Google Account, drastically reducing the chances of having the personal information in your account stolen. To break into an account with 2-Step Verification, bad guys would not only have to know your username and password, they'd also have to get a hold of your phone."
Now There's 2-Step Verification with Security KeyTo make things even more secure, Google is providing another option for the two-step verification process, strengthening it and perhaps even simplifying it. Where users had to login with their password and then type in the security code sent to their phone, this new method requires a password and physical key to be connected to a USB port on your PC, Mac, or Chromebook. Note that the option for using the verification code is still there. As Google states on their blog, this new Security Key feature makes it even harder for a security lapse to occur."Security Key is a physical USB second factor that only works after verifying the login site is truly a Google website, not a fake site pretending to be Google. Rather than typing a code, just insert Security Key into your computer's USB port and tap it when prompted in Chrome. When you sign into your Google Account using Chrome and Security Key, you can be sure that the cryptographic signature cannot be phished."While someone could technically find your phone number and hack your password or setup a fake Google page (to phish) for your password, even if they get it, it'd be physically impossible for them to login without also getting their hands on your Security Key. On the flip side, if someone stole your Security Key, they would need your password for it to be of any use.The new login process adheres to the Universal 2nd Factor (U2F) protocol from the FIDO Alliance. What does that mean? Since these keys are being built using the open-source FIDO standard, other sites could incorporate the same security measures, meaning you could log into Facebook or Outlook with your password and that same USB Security Key. This also mean that flash drive in your drawer probably isn't up to protocol.You can find compatible USB keys on Amazon or from other retailers for anywhere from $6 to $60, depending on the supported protocols and form factor. Here are the compatible keys Google recommends that support FIDO U2F Authentication:Plug Up International Yubico Yubico NEO-n Yubico NEO
What Else Should I Know?This process also does not have to be limited to USB. In the future, expect to see Bluetooth, NFC, and other methods creep into this arena. Here are some more things you should know.
1. Gotta Love ChromeUsing the Security Key with Gmail only works on Chrome. If you use another browser to log into your Gmail account, you will have to use the regular login or the classic two-step verification method.
2. Make Sure Your System Is SupportedTo use a Security Key, you'll need a computer running Google Chrome version 38 or newer on Chrome OS, Windows, Mac OS X, or Linux.
3. You Need a USB PortYou cannot use the Security Key on a device without a USB port. Now this may seem obvious, but for people that use their phone or tablet, you will not be able to log in this way. There are some Security Keys, like the Yubico NEO, that support NFC, but U2F does not by default just yet. So, you will need to use the standard two-step verification with your cell phone number. Image via Yubico
4. Don't Lose ItIf you lose your security key, you will have to buy another one, and that sucks.
5. No Data or Battery RequiredUnlike the mobile phone method, you will never be stuck unable to login because your phone is dead and cannot receive the code. Your Security Key will work whenever, wherever (unless, of course, your laptop is dead and you forgot your cord). You just need to have it on hand. A keychain isn't a bad place to put it.
6. You Can Use Any Supported KeyIf you want to have one key to use at work and another key to use at home, you can do that. The key is just one step of the process and isn't coded to your particular account. Your password and login information is your identifier; the key just confirms that you are on a safe-to-use Google site.Again, here are the keys Google recommends:Plug Up International Yubico Yubico NEO-n Yubico NEO Learn more about using a Security Key here.There are many businesses that use a similar process, but this is one of the few times it's being made for a giant consumer population like Google's. Single-step verification is what many people are used to, as it's easy to do.For those looking for more security on their Gmail and all the other sensitive information Google has on you, the two-step process is a safer route to take. Especially considering the fact that your email account is the key to all of your other accounts, since most websites allow you to reset your password via email."There is no doubt that a new era has arrived," said FIDO Alliance President Michael Barrett in an official statement. "We are starting to move users and providers alike beyond single-factor passwords."Once you've purchased your key, get started with the new two-step verification process here.
Cover image via Shutterstock
Apple however, deems an iPhone ineligible for service if it shows intentional tampering or damage, is a disassembled unit or missing parts, contains non-Apple batteries, or is damaged
Water Damage and replacement - Apple Community
With Windows 10 spying, Microsoft is becoming the new Google of data theft and using the same for serving you advertisements. For hitting the final nail in coffin, you need to click on this link
How to Prevent Microsoft From Spying on You in Windows 10
How to Install TWRP Recovery on OnePlus 6 • Android Jungles
SoundCloud is one of the most popular music streaming services for good reason. You can upload your own music, listen to remixes from your favorite DJ, check out the latest releases from mainstream artists, and even discover new artists. But while you've always been able to listen to most songs for
The Beginner's Guide to SoundCloud - mashable.com
Sep 12, 2017 · After four months of testing, iOS 11 beta testers can now nab the Golden Master just before it's released to the public. Here's how.
Here's how you can get iOS 11 now | ZDNet
News: iOS 11.4.1 Beta 4 Released for iPhones, Includes Only 'Bug Fixes' & Unknown Improvements News: Apple Releases First iOS 12.1 Beta to Software Developers, Brings Back Group FaceTime News: iOS 11.3 Beta 5 Released with Mostly Under-the-Hood Improvements
Apple Releases iOS 10.3.3 with Bug Fixes and Security
You have a webcam, right? Nowadays, who doesn't? But just because you all have webcams doesn't mean you're using them the same way. And a great way to take full advantage of your peripheral or built-in webcam is by turning it into a security camera.
25+ Applications to turn your Webcam into Home Security
9. Create a collection of saved posts. In addition to being able to view all of the posts you've liked, Instagram also has an option to save or bookmark certain posts in collections that you create. Start by going to your profile, and tapping the bookmark icon on the top-right menu above your photos.
How to view photos I've previously liked on Instagram from my
Bluetooth is not just useful for exchanging files between mobile devices, but it can be used to transfer files between a phone and a laptop and even from one laptop to another laptop. You just need to make sure that the laptop you are using has the Bluetooth support.
How To Use Bluetooth File Transfer Between Devices
How To: It's Raining Sweets and Treats! How to Make Your Own Pneumatic Candy Cannon How To: Make a PVC Hand Pump to Move Water, Compress Air, & Create Vacuum How To: Build a high-powered air cannon that shoots rolled up T-shirts How To: Make a Super Cheap One-Way Check Valve
A Simple Compressed Air Cannon Made from PVC Pipes! Powerful
Running diagnostics on your Android phone can be a very tedious process. More often than not, you need to key in dialer codes to see if your device's hardware is functioning properly, though you can also download apps — but these are often hard to understand for a layperson.
How to Test Your Samsung Phone by Using Secret Code - Android
News: Here's Everything We Know About That Nasty iPhone 8 Delay Rumor News: Coming Soon to a Smartphone Near You: 3D Navigation for Buildings! News: Xiaomi Might Make Its First Stop on US Shores with the Mi 8 Anniversary Edition News: Apple's Newest Venture Is Unlike Anything It's Done Before
Everything You Need to Know About the iPhone 8 & 8 Plus « iOS
Review: Motorola Droid with free Google Maps Navigation
Here, you can also select a box that will delete all the app activity from Facebook. But proceed with caution! This step can remove page apps & posts made to your pages or profile .
The problem is, how can the webmaster check out how his/her site look like on a mobile device, if he/she does not own a smartphone? Fret not, with a little trickery, you can easily use your desktop browser to access your site and make it think that you are using a mobile browser. Every browser comes with its own user-agent.
Firefox browser blocks sites and advertisers from tracking
0 comments:
Post a Comment